Uncover Your Organization's Shadow IT
DataFence automatically discovers and catalogs every cloud application your employees use, giving you unprecedented visibility into potential security risks.
Automatic Application Discovery
Our intelligent discovery engine continuously monitors user activity to identify cloud applications and services being used across your organization:
- Cloud storage services (Dropbox, Google Drive, OneDrive)
- Communication platforms (Slack, Discord, Teams)
- AI tools (ChatGPT, Claude, Midjourney)
- Development tools (GitHub, GitLab, CodePen)
- Analytics and productivity apps
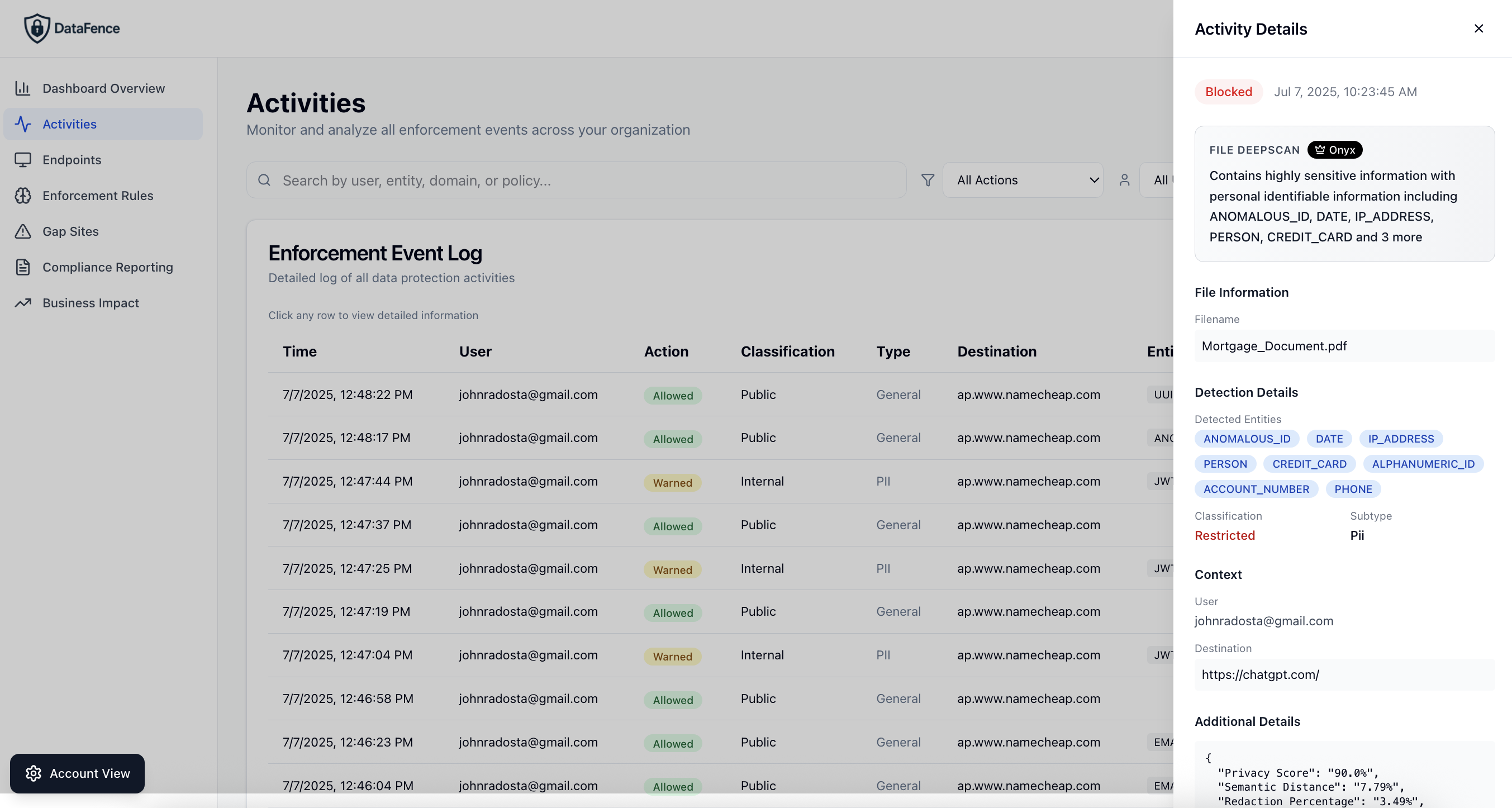
Risk Assessment & Scoring
Each discovered application is automatically assessed for security risks based on multiple factors:
- Security posture: Encryption, authentication methods, compliance certifications
- Data exposure: Types of data being shared or stored
- User adoption: Number of users and frequency of use
- Compliance impact: Regulatory implications
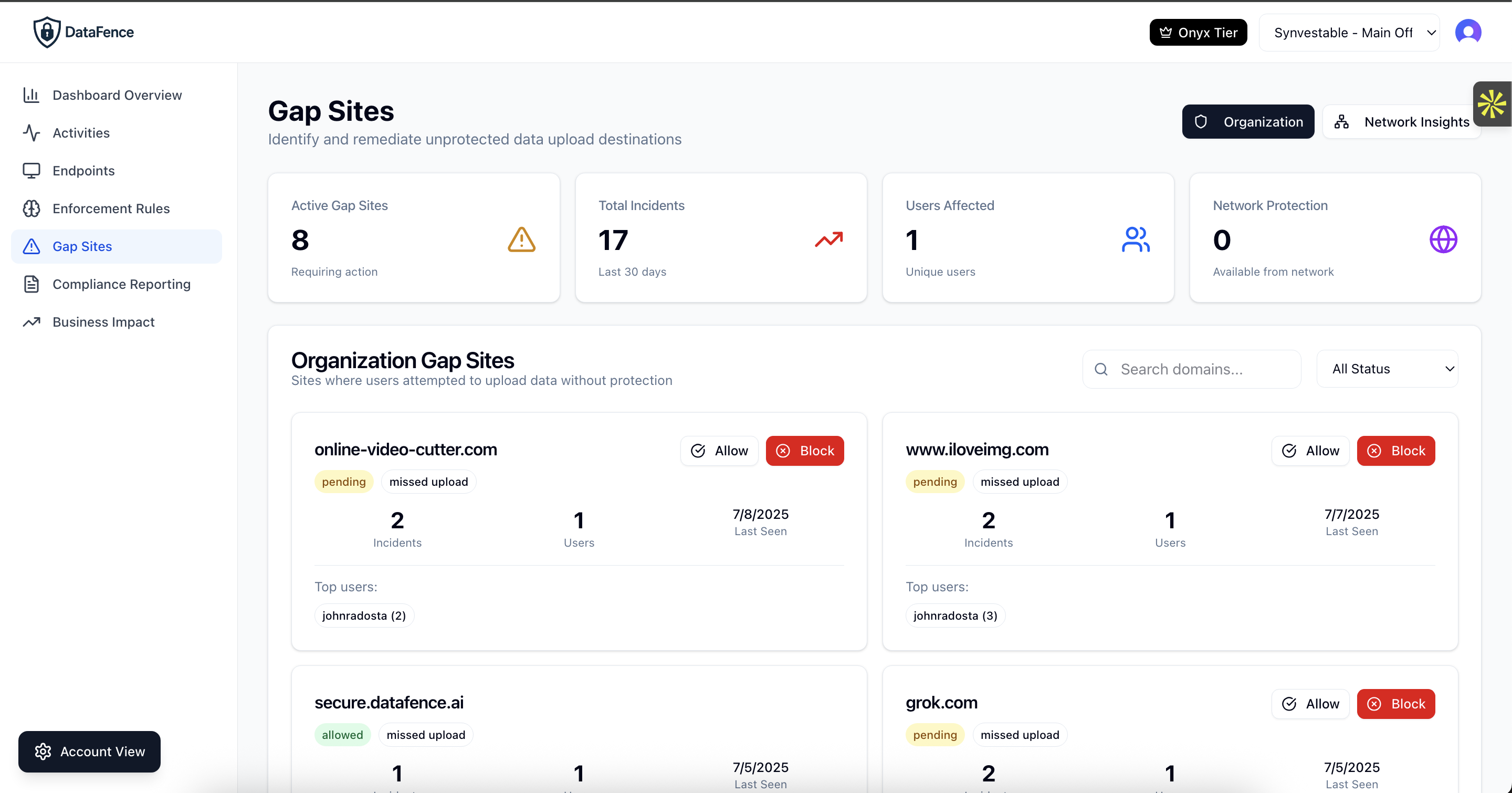
Shadow IT Discovery Features
Gap Reports
Identify applications where data is flowing but no security policies exist. Prioritize which apps need immediate attention.
Network Intelligence
Leverage crowdsourced insights from the DataFence network to understand emerging shadow IT trends and risks.
User Analytics
See which departments and users are adopting unsanctioned apps. Understand usage patterns and business needs.
Automated Blocking
Instantly block high-risk applications or set policies to warn users before accessing unsanctioned services.
Sanctioning Workflow
Streamline the process of evaluating and approving cloud applications with built-in assessment workflows.
Executive Reporting
Generate board-ready reports showing shadow IT risks, trends, and remediation progress over time.
Why Shadow IT Discovery Matters
Reduce Data Breach Risk
Unknown applications represent unknown risks. By discovering shadow IT, you can prevent data breaches before they happen.
Ensure Compliance
Meet regulatory requirements by maintaining a complete inventory of where sensitive data is being processed and stored.
Optimize IT Spend
Discover duplicate services and consolidate to approved alternatives, reducing costs and complexity.
Enable Innovation Safely
Understand what tools employees need and provide secure alternatives that meet both business and security requirements.
Discover Your Shadow IT Today
Get complete visibility into your organization's cloud application usage